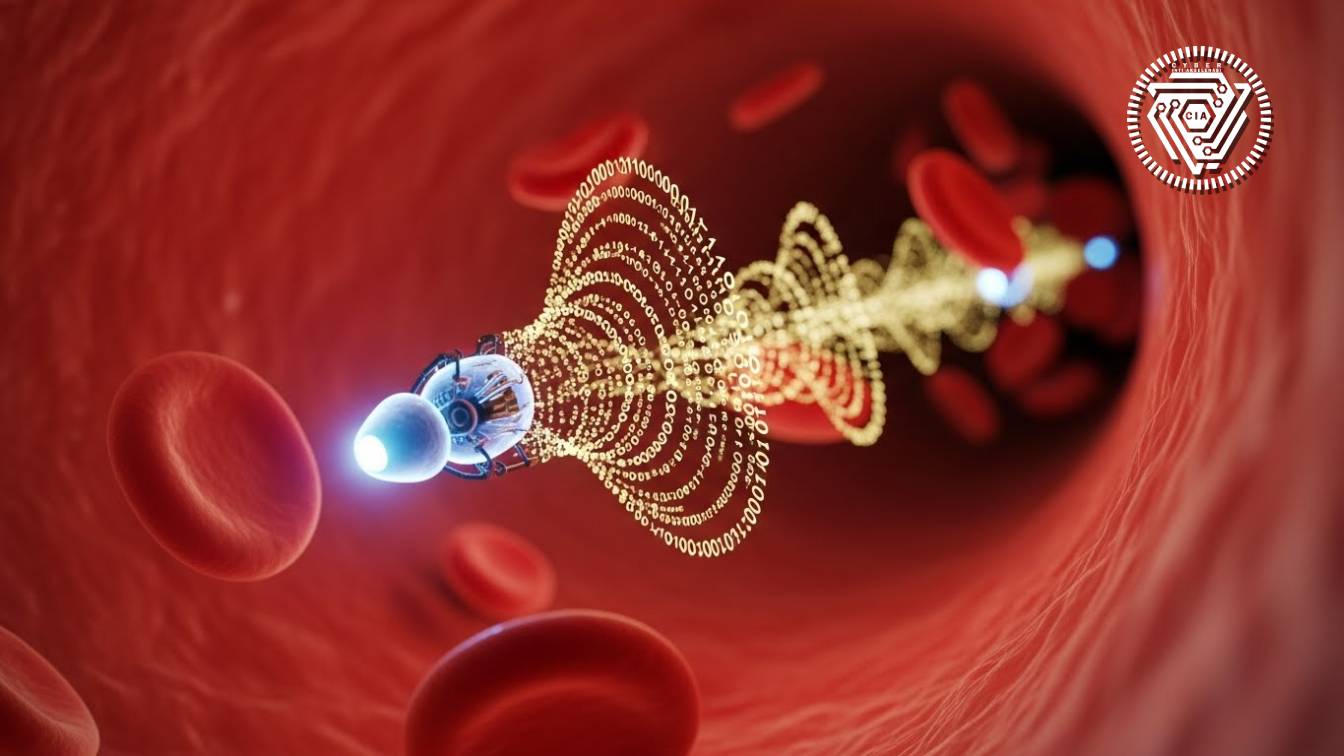
If we think IoT (Internet of Things) is the peak of connectivity, we are dead wrong. In 2026, the new technological frontier is no longer in the cloud, but inside our blood vessels. This is the era of the Internet of Bio-Nano Things (IoBNT). Unlike conventional IoT which uses electromagnetic waves, IoBNT uses Molecular Communication (MC). Recent scientific studies from the IEEE Communications Surveys & Tutorials journal explain that we are now able to engineer bacteria or synthetic cells to become 'nanomachines' that transmit data using chemical molecules, exactly how hormones work, but digitally programmed.
Scientific Study: Signal Propagation Challenges
The biggest challenge in IoBNT is not building the sensors, but the communication 'channel'. In standard wireless networks, we deal with frequency noise. In the human body, we deal with fluid diffusion, blood flow, and enzymes that might 'eat' the data packets (molecules) before they reach their destination. Recent research uses Quorum Sensing techniques—a natural bacterial communication mechanism—to amplify data signals so they can penetrate the noisy biological environment without triggering an immune response.
Medical and Ethical Implications
Imagine the implications: Nano sensors swimming in your arteries could detect stage 0 cancer cells, then send an 'alert' signal to your smartwatch, or even directly command the release of chemotherapy drugs right at the cancer site (targeted delivery). This radically shifts the medical paradigm from 'reactive' to 'preventive-proactive'.
However, as IT experts at CybermaXia, we must critically view the security aspect. If our bodies are connected to a network, then our bodies can be hacked. 'Bio-Cyber' attacks where hackers manipulate insulin signals or heart rates are no longer science fiction, but a new category of cybersecurity threat that we must anticipate with encryption protocols starting now.